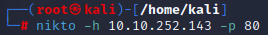Web Enumeration | THM
February 15, 2023
Practical: Gobuster
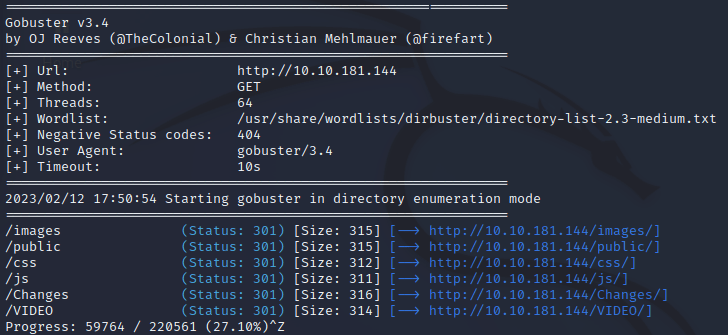
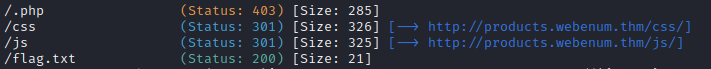
Run a directory scan on the host. Other than the standard css, image and js directories, what other directories are available?
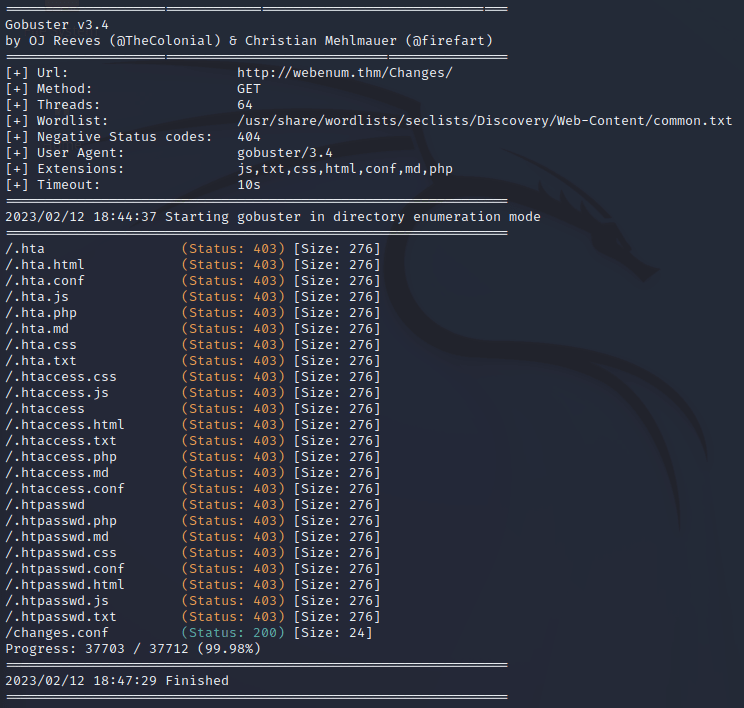
Run a directory scan on the host. In the C****** directory, what file extensions exists?
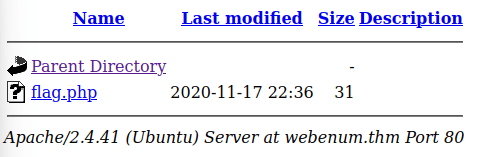
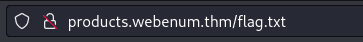
There's a flag out there that can be found by directory scanning! Find it!
The easier way to do this is by navigating through the directories we found in the previous scans.
There are some virtual hosts running on this server. What are they?
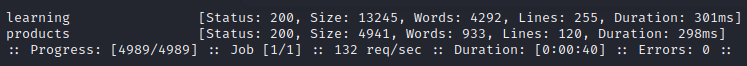
Since Gobuster is not giving me the result that I wanted, I decided to look for a way around the problem and find that ffuf works. So I used that for this problem.
There's another flag to be found in one of the virtual hosts! Find it!
The code above will perform a Gobuster scan against both vhost at once.
Once you got the path you can just browse to it to see the flag.
Practical: WPScan
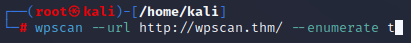
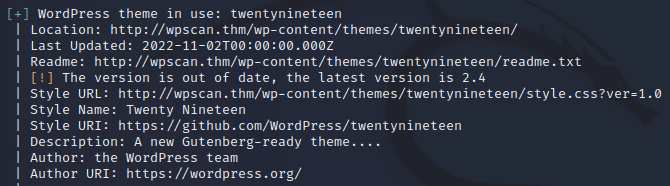
Enumerate the site, what is the name of the theme that is detected as running?
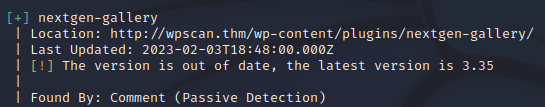
Enumerate the site, what is the name of the plugin that WPScan has found?
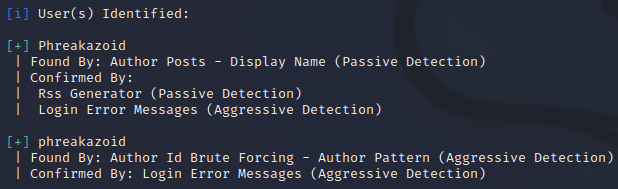
Enumerate the site, what username can WPScan find?
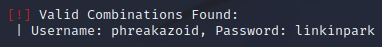
Construct a WPScan command to brute-force the site with this username, using the rockyou wordlist as the password list. What is the password to this user?
Practical: Nikto
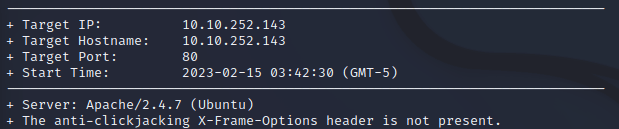
What is the name & version of the web server that Nikto has determined running of port 80?
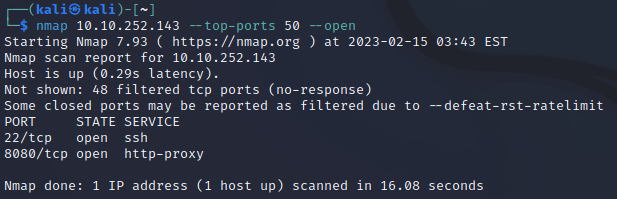
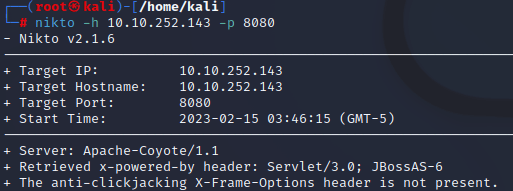
There is another web server running on another port. What is the name & version of this web server?
You can do a nmap scan first to see which ports are open.
Now you can scan it with nikto.
What is the name of the Cookie that this JBoss server gives?